Security Architecture Overview
Security Architecture Overview
We maintain a comprehensive internal security model covering network segmentation, authentication workflows, and access isolation. Detailed security architecture diagram outlining these components is available under NDA for enterprise customers.
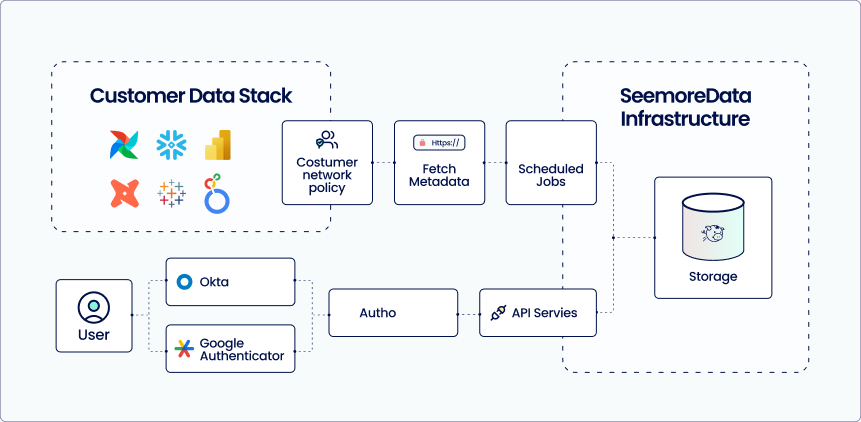
High level diagram of our solution
Cloud Infrastructure
Our platform is deployed entirely in Amazon Web Services (AWS), leveraging high-availability, auto-scaling services configured with AWS-native security tooling and compliance features. This allows us to maintain resilient and fault-tolerant systems while adhering to best practices for cloud security.
All infrastructure resources are provisioned and maintained using Infrastructure as Code (IaC), ensuring that environments are reproducible, controlled, and auditable
Network Security & Customer Connectivity
We support fixed IP address policies to allow customers to safely whitelist Seemore Data traffic within their Snowflake environments. Network egress from our systems can be explicitly scoped to known IP ranges, providing full transparency and control over integration behavior.
Authentication to Customer Environments
Authentication to customer environments—particularly Snowflake—is secure, tightly scoped, and read-only by design.
- Dedicated Read-Only Snowflake Users:
Each customer is provisioned a Snowflake user account with access limited to metadata schemas like INFORMATION_SCHEMA, ACCOUNT_USAGE, and ORGANIZATION_USAGE. These permissions ensure that Seemore Data cannot view, write, or alter raw business data under any circumstances. - Key-Pair Authentication:
Instead of passwords or API tokens, we authenticate via public/private key pairs. Private keys are securely generated and encrypted within our platform, while public keys are registered in the customer’s Snowflake instance. This setup eliminates reliance on shared secrets and significantly reduces exposure to credential-based attacks. - Customer Network Controls:
Customers can apply strict IP allow-listing and maintain full control over who and what can connect to their Snowflake environment from Seemore Data. - Session Boundaries:
Connections from Seemore Data are ephemeral and stateless. Sessions are time-bound, scoped, and rate-limited to avoid any risk of performance degradation or misuse.
Zero Data Ingress Model
Seemore Data adheres to a zero data ingress principle. We never ingest, store, or modify customer data. Our platform interacts exclusively with metadata—strictly limited to the scope you authorize. SQL statements executed are fully visible to your team and available for audit.
Customers who opt in may enable write-level permissions to allow Seemore to perform controlled infrastructure operations—such as resizing warehouses or adjusting schedules. These actions are governed by clear permission boundaries and customer consent, with complete transparency and logging.
Access Logging & Auditability
All access is logged both within Snowflake and on our internal systems. Snowflake’s native access history logs every connection and query run via our integration. In parallel, Seemore retains internal telemetry to track system behavior, monitor authentication flows, and support audit requests. Audit summaries are available to enterprise customers upon request
Secure Software Development Lifecycle (SDLC)
Security is deeply embedded into every phase of our engineering process:
- Shift-Left Security:
Security reviews begin at the earliest phases of development, ensuring vulnerabilities are addressed before code is merged or deployed. - Test-Driven Development (TDD):
Engineers write tests before implementation to define expected behavior. We maintain high test coverage across our services, ensuring every release is stable and reliable. - Peer Review & Security Gates:
All code is peer-reviewed, and merges to protected branches require passing:- Linting & static code analysis
- Security policy compliance
- Dependency scanning for known vulnerabilities
- CI/CD Pipelines:
We use automated pipelines to validate and deploy changes. These pipelines:- Enforce signed commits
- Run security scans in parallel with builds
- Deploy using declarative templates (e.g., Terraform)
- Environment Isolation:
Dev, staging, and production environments are fully separated. Staging mirrors production to ensure accurate pre-deployment testing. - Secrets Management:
Sensitive credentials are never stored in code. We rely on AWS Secrets Manager to manage and rotate secrets securely. - Audit & Rollback:
Each deployment is versioned, logged, and monitored. In the event of any issue, changes can be rolled back automatically to the last known good state
Physical & Environmental Security
By hosting exclusively in AWS, we benefit from data centers with top-tier physical security controls, including surveillance, biometric access systems, and environmental monitoring. AWS’s global infrastructure complies with numerous certifications and frameworks (e.g., SOC 1/2/3, ISO 27001, and PCI DSS), providing strong foundational controls for our own security posture